Working Remotely with your Protected Health Information (PHI)
What computer should I use? Can I use my home computer?
When working with PHI data we require that you use a properly managed and encrypted university-owned computer. This ensures security checks and computer updates that the central IT division can verify for compliance needs. If you have a specific need for a university owned computer to work remotely with PHI data please work with submit a request via our “I Need Tech” website to request a device. You should, under no circumstances, use your home computer for Interacting with PHI related data.
What do I need on my computer to make sure I can securely access PHI data?
We require that your computer has the following software on it for secure data use. Please reach out to your local IT support if you have any issues installing the software.
- The KSU-VPN, Global Protect – Your university laptop should have this software by default, but if it’s not present you may download it by visiting http://software.kent.edu/. Search for “VPN”, click the “View Details” button, and then follow the on-screen instructions for downloading and installing the software.
- Microsoft Teams – You may visit the KSU Keep On Working Microsoft Teams page to get started with Microsoft Teams. Not only does the page contain links to tons of useful information on using Microsoft Teams it also directs you do the download page for the software. Microsoft Teams is fully HIPAA compliant and is our recommended tool for transmission of PHI data and video conferencing needs involving PHI.
How do I make sure my network connection is safe while working with PHI data?
Make sure your home WiFi is secured. Ensure that your wireless network has a password required to access it and that you are not using the default password for your wireless network but, instead, a unique complex password. Please contact your internet service provider (AT&T, Spectrum, etc.) or router manufacturer for guidance on changing your wireless password, if needed.
If you’re at home on your WiFi or on a cellular hotspot please connect to the VPN to guarantee your data is encrypted in transit. Use the Global Protect VPN whenever you are off-campus and interacting with PHI data. Do not access PHI data in public locations nor via any public networks (e.g. Starbucks) even with the VPN connected. Unsecured public WiFi does not meet Kent State’s expectations for privacy and security as it relates to interacting with PHI remotely.
How do I store PHI data securely?
I need to store PHI for access later...
Use Microsoft Teams and Microsoft OneDrive for PHI data storage. As mentioned above, Microsoft Teams is fully HIPAA compliant and is a safe way to store, access, and transfer PHI data. Please note that we do recommend only accessing PHI data from these sources while on university owned devices.
Can I store PHI on removable media?
Use of removable media to store PHI data is prohibited. Please do not save any PHI data to a USB flash drive, an external hard drive, or any similar storage device. If you need assistance with transferring PHI please contact Aaron Near, anear@kent.edu.
What if I want to store PHI on my personal Google or iCloud?
Do not store PHI data in personal Google Drive, iCloud, or any other similar non-Kent State associated Microsoft cloud storage solutions. All Kent State PHI must be stored on Kent State approved storage.
I know email is not secure, but is there a way for me to send a secure email message to a client with my Kent State email account?
Yes, you are required to encrypt email containing PHI data that you are sending with your Kent State email account.
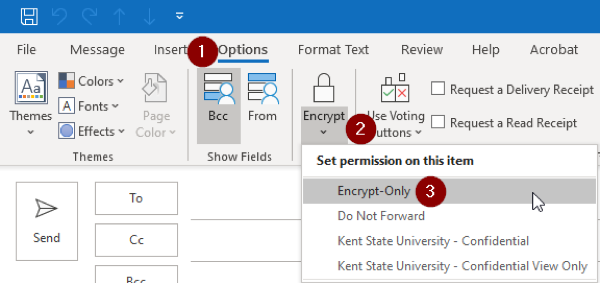
- In Outlook on your Windows or Mac computer choose Options (1), select Encrypt (2), and then select Encrypt-Only (3).
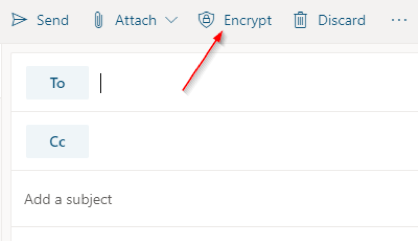
- In Outlook Web Access (OWA) click the “Encrypt” button just above the “To:” line
Reading encrypted messages is a seamless process when sent to other Office 365 / Exchange accounts at Kent State – there will just be a padlock icon displayed in above the body of the email message. When sending encrypted messages to students at Kent State the students are likely to have KSU Gmail accounts. There is an extra set of steps the student will need to perform in order to read the message using a one-time passcode (OTP). You may see an outline of these steps on the Microsoft email blog.
I need to setup a video conference to talk with a client or to discuss PHI data with colleagues at the university, what do I use?
We strongly recommend Microsoft Teams as your PHI and HIPAA compliant video conferencing solution. If you have an Office 365 / Exchange email account with Kent State, then you have the ability to schedule meetings in Microsoft Teams. This will allow you to schedule meetings ahead of time with your clients or colleagues.
If you are not using Microsoft Teams, you need KSU Information Security to approve and verify the video conferencing solution is HIPAA compliant.
What are the steps I need to take to schedule a meeting with a client or colleague?
To schedule a meeting in Microsoft Teams please refer to the "Teams Meetings - Host - Scheduling a Meeting" guide.
When it’s time for the video conference what do I do? What do my clients need to do?
To start a meeting in Microsoft Teams please refer to the "Teams Meeting - Host - Starting a Meeting" guide.
For clients, we ask that you please distribute the "Teams Meetings - Client Experience" guide at least 24 hours prior your scheduled meeting session with them.
Can I record my video conference Teams meetings?
Absolutely. Teams meetings can be recorded via the settings once a meeting starts – there’s a “Start Recording” option you need to click. It’s important to note that recording a session should only be done with the consent of all parties involved. Please follow the appropriate guidelines for recording consent for your department.
Recordings of Teams meetings are stored in Microsoft Stream. The default permissions for the recording are setup so that only the creator of the meeting and invitees on the meeting can access the video. It is very important to note that you should be very careful when changing sharing permissions as the default sharing option shares the meeting with everyone in the organization. You must restrict your shared videos to just individual people if you absolutely must share your video records. Please following these Microsoft Stream instructions for sharing with individuals. There is a delay of an hour or so once a video conferencing session ends before the recording will be processed and accessible via Microsoft Steam. You will receive an email with a link once the recording is available.
We strongly recommend that any recordings should not be altered in anyway if downloaded.
I need to make a phone call to one of my patients, how can I do that without being in my office with access to my desk phone or using my personal cell phone?
We’ve got you covered with the program Cisco Jabber. Jabber essentially turns your computer into a phone – you can dial numbers on-campus and off-campus and they will appear as if the calls are originating from your desk phone. You will also receive calls coming into your extension on your computer. You can also check your voicemail from Jabber! One thing to double-check is if your computer has a microphone – a good rule of thumb is that if you have a webcam on your computer you also have a microphone. If you need a USB headset because your computer does not have a microphone built-in please submit a request on the I Need Tech website.
For more information on Cisco Jabber visit the Collaboration page on the Keep on Working site.
Additional security and privacy requirements that you need to be aware of.
The most important things to consider are privacy and security. If you have followed the recommendations outlined above, you likely have the security aspect completed.
Please remember to be considerate of privacy as well when you’re accessing PHI data, watching recordings of video conferences, or hosting a call. Other people in your home should not be able to hear or see any part of the PHI data or sessions. To be clear, under no circumstances should you share the computer you use for accessing PHI data with other people (friends, family, etc.) Also, when accessing PHI data, make sure you are alone in a private setting. You should not under any circumstances access or hold conference sessions in public settings (e.g. Panera or a library). Your computer screen should not be visible by anyone in the household but you. If you require a privacy cover for your computer screen please submit a request via our “I Need Tech” website.
If you have physical PHI data at your house (e.g. client notes) it must be kept in a locked file cabinet or safe when you are not using it. Once it is no longer needed it must be run through a shredder.
If you experience any issues with your university owned computer while working from off-campus please reach out to your local IT support for assistance.
If you have questions about working with PHI remotely that are not addressed or would like clarification on any of the content here please contact Aaron Near, anear@kent.edu, from the Division of Information Technology.
